Information Security and Privacy Protection
- 8




Information Security
In order to ensure the confidentiality, integrity, usability and legality of information assets, Qisda formulates the Information Security Policy in accordance with the ISO 27001:2022 form BSI international information security standards, forms an information security management committee, and organizes information security online education courses for all employees to improve colleagues’ information security awareness.
In order to reduce the loss of the company,Qisda has taken out corporate information security risk management insurance with insurance claims for related expenses (such as operation interruption, forensics) when information security incidents occur.
Information security risk analysis average score
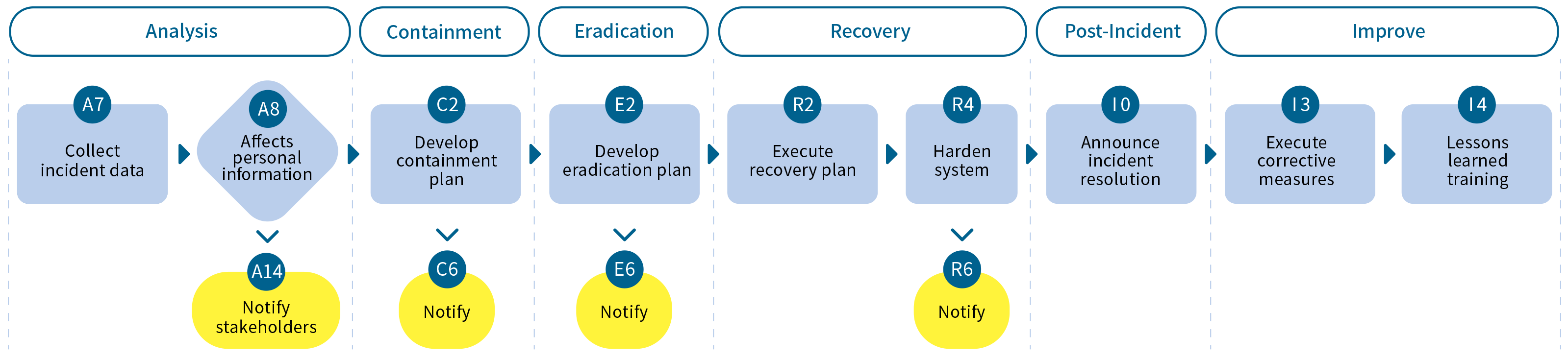
Measures for Significant Information Security Incidents
During the establishment of the ISMS, Qisda has enhanced the SOP and organized a series of drills to improve the emergency response process. We will continue to conduct simulations for different information security attack incidents with related personnel participating in the drills, in order to ensure that we can kick off the emergency process when the incident happens and effectively lower the response time and losses on the Company. In 2024, information security incident 0 occurred.
Information Security Reporting and Handling Process
Privacy Protection
Qisda values and strives to protect privacy and personal data.Referencing to local laws and regulations related to protection of the right to privacy of each operation location along with the EU “General Data Protection Regulation (GDPR),” we have established the Privacy Policy of Qisda Corporation to protect all personal data.We also required the subsidiaries, joint ventures, suppliers, contractors, external consultancies and subcontractors to meet the policies in the hope of protecting the right of the personal data owner.
In 2024, no complaint was received due to the occurrence of incidents related to data loss or leak.
Personal data leaks

Customer Privacy Management Framework
Data Protection
- Access rights are established, and access to data by unrelated personnel requires approval through supervisor endorsement before partial permissions are granted.
- Documents downloaded are labeled with the word 'Confidential' to remind users of their sensitive nature.
Internal Controls
- Periodically educate employees on the importance of information security.
System Management
- Customers with account credentials can access system website data but only within the scope of relevant business.
- New account passwords are sent to customers through system-generated messages, ensuring that internal personnel do not have access to them. This ensures that the account is used solely by the applicant.
Number of complaints about personal data leaks | 2024 | 2023 | 2022 | 2021 |
|---|---|---|---|---|
External agency | 0 | 0 | 0 | 0 |
Customers reflection | 0 | 0 | 0 | 0 |
Unit:Number of complaints




Want to know more detailed content?
Read Report Contents